How To Use a Virtual Private Network (VPN)
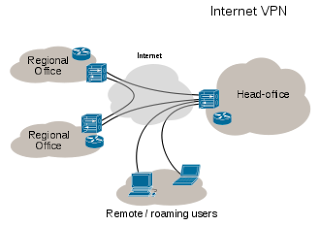 A virtual private network (VPN) extends a private network across a public network, such as the Internet. It enables a computer to send and receive data across shared or public networks as if it were directly connected to the private network,while benefiting from the functionality, security and management policies of the private
A virtual private network (VPN) extends a private network across a public network, such as the Internet. It enables a computer to send and receive data across shared or public networks as if it were directly connected to the private network,while benefiting from the functionality, security and management policies of the privatenetwork.
OPEN VPN
OpenVPN is a fairly new open source technology that uses the OpenSSL library and SSLv3/TLSv1 protocols, along with an amalgam of other technologies, to provide a strong and reliable VPN solution. One of its major strengths is that it is highly configurable, and although it runs best on a UDP port, it can be set to run on any port, including TCP port 443. This makes it traffic on it impossible to tell apart from traffic using standard HHTP over SSL (as used by for example Gmail), and it is therefore extremely difficult to block.
Another advantage of OpenVPN is that the OpenSSL library used to provide encryption supports a number of cryptographic algorithms (e.g. AES, Blowfish, 3DES, CAST-128, Camellia and more), although VPN providers almost exclusively use either AES or Blowfish. 128-bit Blowfish is the default cypher built in to OpenVPN, and although it is generally considered secure, it does have known weaknesses, and even its creator was quoted in 2007 as saying ‘At this point, though, I’m amazed it’s still being used. If people ask, I recommend Twofish instead’.
AES is the newer technology, has no known weaknesses, and thanks to its adoption by the US government for use in protecting ‘secure’ data, is generally considered the ‘gold standard’ when it comes to encryption. The fact that it has a 128-bit block size rather than Blowfish’s 64-bit block size also means that it can handle larger (over 1 GB) files better than Blowfish. However, both ciphers are NIST certified, which while not widely recognised, we view as a serious problem. See below for a discussion about this.
How fast OpenVPN performs depends on the level of encryption employed, but it is generally faster than IPsec.
OpenVPN has become the default VPN connection type, and while natively supported by no platform, is widely supported on most through third party software (including now on both iOS and Android).
Compared to PPTP and L2TP/IPsec, OpenVPN can be a bit fiddly to set up. When using generic OpenVPN software in particular (such as the standard open source OpenVPN client for Windows), it is necessary to not only download and install the client, but also to download and setup additional configuration files. Many VPN providers get around this configuration problem by supplying customized VPN clients.
Perhaps most importantly in light of the information obtained from Edward Snowden, it seems OpenVPN has not been compromised or weakened by the NSA, and is also (thanks to its use of ephemeral key exchanges, as we will discuss later) immune to NSA attacks on RSA key encryption. Although no-one knows the full capabilities of the NSA for sure, both the evidence and the mathematics strongly point to OpenVPN, if used in conjunction with a strong cipher, being the only VPN protocol that can be considered truly secure.
Another advantage of OpenVPN is that the OpenSSL library used to provide encryption supports a number of cryptographic algorithms (e.g. AES, Blowfish, 3DES, CAST-128, Camellia and more), although VPN providers almost exclusively use either AES or Blowfish. 128-bit Blowfish is the default cypher built in to OpenVPN, and although it is generally considered secure, it does have known weaknesses, and even its creator was quoted in 2007 as saying ‘At this point, though, I’m amazed it’s still being used. If people ask, I recommend Twofish instead’.
AES is the newer technology, has no known weaknesses, and thanks to its adoption by the US government for use in protecting ‘secure’ data, is generally considered the ‘gold standard’ when it comes to encryption. The fact that it has a 128-bit block size rather than Blowfish’s 64-bit block size also means that it can handle larger (over 1 GB) files better than Blowfish. However, both ciphers are NIST certified, which while not widely recognised, we view as a serious problem. See below for a discussion about this.
How fast OpenVPN performs depends on the level of encryption employed, but it is generally faster than IPsec.
OpenVPN has become the default VPN connection type, and while natively supported by no platform, is widely supported on most through third party software (including now on both iOS and Android).
Compared to PPTP and L2TP/IPsec, OpenVPN can be a bit fiddly to set up. When using generic OpenVPN software in particular (such as the standard open source OpenVPN client for Windows), it is necessary to not only download and install the client, but also to download and setup additional configuration files. Many VPN providers get around this configuration problem by supplying customized VPN clients.
Perhaps most importantly in light of the information obtained from Edward Snowden, it seems OpenVPN has not been compromised or weakened by the NSA, and is also (thanks to its use of ephemeral key exchanges, as we will discuss later) immune to NSA attacks on RSA key encryption. Although no-one knows the full capabilities of the NSA for sure, both the evidence and the mathematics strongly point to OpenVPN, if used in conjunction with a strong cipher, being the only VPN protocol that can be considered truly secure.
Pros
- Highly configurable
- Very secure (probably even against the NSA)
- Can bypass firewalls
- Can use a wide range of encryption algorithms
- Open source (and can therefore be readily vetted for back doors and other NSA style tampering)
Cons
- Needs third party software
- Can be fiddly to set up
- Support on mobile devices is improving, but is not as good as on the desktop






This professional hacker is absolutely reliable and I strongly recommend him for any type of hack you require. I know this because I have hired him severally for various hacks and he has never disappointed me nor any of my friends who have hired him too, he can help you with any of the following hacks:
ReplyDelete-Phone hacks (remotely)
-Credit repair
-Bitcoin recovery (any cryptocurrency)
-Make money from home (USA only)
-Social media hacks
-Website hacks
-Erase criminal records (USA & Canada only)
-Grade change
-funds recovery
Email: onlineghosthacker247@ gmail .com